Tuesday, October 25, 2016
vvv Extension how recover Ransomware Removal Guide
vvv Extension how recover Ransomware Removal Guide
If all of a sudden, most of your files have become unreadable and they all end with a .vvv extension then your computer is infected with a new variant of TeslaCrypt ransomware. Some anti-virus engines detect it as TR/Crypt.ZPACK. This ransom virus leaves multiple files called how_recover+*.txt and how_recover+*.html on your computer with information on how to decrypt your files. There cant be many of us who dont know about the plethora of malicious software, phishing scams, data breaches and other threats that are increasingly sophisticated ? and increasingly unpleasant ? as they do their level best to defraud, con, threaten, frighten and rob us. Unfortunately for the likes of us, the only real way to safeguard our data, bank accounts, and sanity, is to stay one step ahead of the latest dangers. And that means knowing what we are dealing with. To that end, in this post we are going to take a look at a type of malware that is often overlooked, despite the fact that thanks to its thoroughly spiteful nature, it really does deserve a little more time in the spotlight. Welcome to your TeslaCrypt 101.
What is TeslaCrypt ransomware?
One reason why ransomware seems to be relatively unknown when compared to malware such as Trojan Horses or spyware is that it goes under a few different aliases. Alternatively called cryptoware, a cryptovirus, cryptoworm or cryptotrojan, if youve stumbled across any of these names before, then you are also reading about ransomware.
Call it what you like, TeslaCrypt ransomware is an extremely dangerous, and worrying, program and something you definitely want to take pains to avoid. If youre wondering just what it is that this malware can do, the names given to the various strains might give you a clue: ransom, crypto... Yes, it is a program that has been designed to infiltrate your computer, kidnap your data by encrypting it, and then demand a ransom for its release (usually $300 or more). The theory is that once you have paid the ransom, you will be sent a code which will allow you to decrypt your files. This particular variant encrypts your files and changes file extensions to .vvv, for example review.docx.vvv. Such encrypted Word documents cannot be opened by any program. You will simply get an error message. What is more, it manages to encrypt files on Dropbox folders. Luckily, Dropbox offers free versioning on all of its accounts which means that you will be able to restore your files from previous versions. Unfortunately, you cant do the same with files stored on your hard drive. This ransomware attempts to delete all previous versions of encrypted files.
Ways that TeslaCrypt is spread
Unfortunately, it is spread in a couple of different ways, so there are a number of things you need to watch out for if you are to avoid becoming prey. If you have visited a website that has been compromised by ransomware you will be infected, or if you open an email attachment or click a link in an instant chat app message that contains the malware, you will also kick start the ransomware process.
What happens during a ransomware attack?
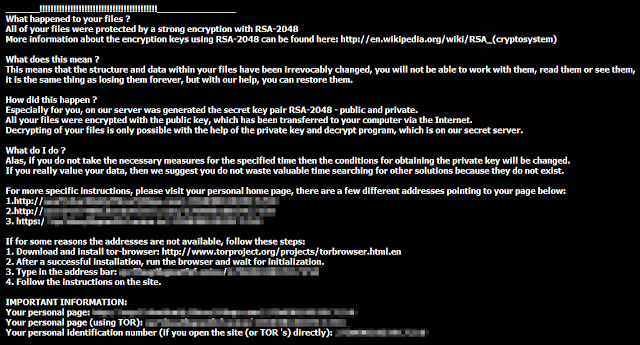
As I said earlier, the way that TeslaCrypt works is to hijack your files and then demand that you pay in order that they are released. However, it is not quite as clear cut as all that and please dont think that by capitulating to the kidnappers demands you will get your data back. Do not lose sight of the fact that we are talking about cyber crime here ? the likelihood of the mastermind behind the program actually caring enough to supply you with the code to decrypt your files once you have paid is... well, not really very likely.
Therefore, if you do receive an email or on screen message telling you your files are being held hostage, dont pay a penny unless you absolutely must and have not other choice.
Should I pay the ransom?
There is NO guarantee that the party responsible will release your files so follow the steps in the removal guide below to remove this ransomware from your computer and hopefully, decrypt your files.
How to get my files back?
If you have a recent backup, wipe your hard disk and reinstall your files. If you dont, try Shadow Explorer and Recuva programs or search your computer for previous versions of files. If you are lucky enough you may find files that were not encrypted and renamed to .vvv. But before restoring your files, please remove the ransomware and related malware files from your computer. To do so, please follow the steps in the removal guide below. If you have any questions, please leave a comment down below. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
Step 1: Removing TeslaCrypt (.vvv extension) ransomware and related malware:
Before restoring your files from shadow copies, make sure the TeslaCrypt is not running. You have to remove this malware permanently. Thankfully, there are a couple of anti-malware programs that will effectively detect and remove this malware from your computer.
1. First of all, download and install recommended anti-malware scanner. Run a full system scan and remove detected malware.
Important! If you cant download or run it, please restart your computer in Safe Mode with Networking or Safe Mode and try again. If you dont know how to do that, please watch this video.
2. Then, download ESET Online Scanner and run a second scan to make sure there are no other malware running on your computer.
Thats it! Your computer should be clean now and you can safely restore your files. Proceed to Step 2.
Step 2: Restoring files encrypted by TeslaCrypt (.vvv extension) virus:
Method 1: The first and best method is to restore your files from a recent backup. If you have been regularly performing backups, then you should use your backups to restore your files.
Method 2: Try to restore previous versions of files using Windows folder tools. To learn more, please read Previous versions of files.
Method 3: Using the Shadow Volume Copies:
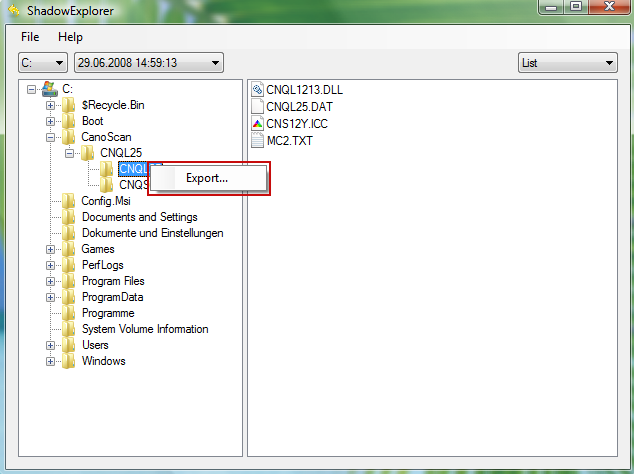
1. Download and install Shadow Explorer. Note, this tool is available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8.
2. Open Shadow Explorer. From the drop down list you can select from one of the available point-in-time Shadow Copies. Select drive and the latest date that you wish to restore from.
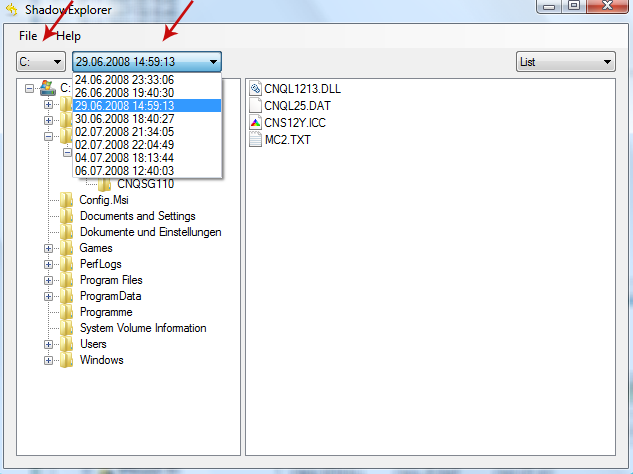
3. Righ-click any encrypted file or entire folder and Export it. You will then be prompted as to where you would like to restore the contents of the folder to.
Hopefully, this will help you to restore all encrypted files or at least some of them.
Available link for download