Showing posts with label security. Show all posts
Showing posts with label security. Show all posts
Tuesday, April 18, 2017
Monday, April 10, 2017
USB Disk Security 6 4 Full Version Free Download
USB Disk Security 6 4 Full Version Free Download

Instuctions:-
Install it
Crack or Give Serial.
Enjoy it
Download Link
Available link for download
Wednesday, April 5, 2017
USB Disk Security 6 5 0 0 Final Cracked Free Download
USB Disk Security 6 5 0 0 Final Cracked Free Download

USB Disk Security uses innovative technology to block known and unknown threats via USB drive. It supports USB drive, flash disk, secure digital card, thumb drive, pen drive, removable storage, ipod, and more.
The best solution to protect offline computer:
Other antivirus software should update virus database regularly, and they cannot effectively protect offline computers that are not connected to the Internet. When new viruses, worms and other malicious attacks strike, traditional signatures are insufficient. Every minute one waits for a virus signature update creates a window of vulnerability that could have devastating consequences. USB Disk Security uses advanced proactive detection techniques, and closes the window of vulnerability left open by other reactive, signature-based responses.
Data Protection:
Deliver high level of protection against theft and accidental disclosure of confidential data. This feature can prevent unauthorized persons from copying your data to USB drives, and it also can stop the threats from USB drive.
Screenshot:

FEATURES:
- Block known and unknown threats from removable media
- Free for personal use
- Prevent unauthorized persons from stealing your data
- Compatible with other security software
- Compatible with all popular Windows platforms
- Fastest and lightest security software
- Best solution to protect offline computer
- UnRAR Using The RAR File
- Run Setup
- It Will Be Auto Install & Registered [Silent Install] (Make It Easy For You)
- Done! :)
Download Now
Available link for download
Monday, April 3, 2017
USB Disk Security v6 8 0 501 Incl Crack Serial Key
USB Disk Security v6 8 0 501 Incl Crack Serial Key

Description:-
USB Disk Security is a good option, especially if you often connect devices from other users to your computer or if many different people use the same machine. Its other features make a nice bonus as well, and the program is completely free to download and use.
Advantage:
When you connect a USB drive to your computer, this program automatically scans it to make sure its not brining any unwanted programs with it. Anything suspect is stuck in Quarantine, where you can take a look at it and decide whether its a threat or not. You can also use the app to secure your own USBs by adding password protection and access control, so you can be sure no one can access your data if you lose your device.
URL scanner:
There are also some nice Web security features included in this program. One of these is the URL Scanner, which lets you enter any URL to see if its a safe one to visit, so you dont endanger your computer while browsing.
Terrible help:
The Help file that comes with this program is a jumble of information, and it doesnt always match up with what you see on your own screen when using the app. While the apps interface is straightforward enough that you shouldnt have much trouble finding the features youre looking for, it would be nice to have a usable reference when problems arise as well.
Requirements:-
Windows XP / Windows 7/ Windows 8 / Windows 8.1 or above With Minimum Requirements
Windows XP / Windows 7/ Windows 8 / Windows 8.1 or above With Minimum Requirements
Previews:-


Download Link:-
 |
Download USB Disk SecurityPassword is: blackeyez007.blogspot.com |
Available link for download
Friday, February 24, 2017
Using iOS 7 to Optimize iPhone Security
Using iOS 7 to Optimize iPhone Security

Managing an iPhone with iOS 7
The bring your own device (BYOD) model for workplace integration has taken off, with more businesses allowing their employees to utilize smartphones, tablets and laptops, in place of their company-provided tools. As if in response to this trend, Apple released iOS 7 with features that enhance the functionality of the iPhone in an office setting.According to TechRepublic, features such as AirDrop make sharing photos and documents fast and simple by connecting employees to one another, enabling a collaborative workplace environment for those who are utilizing this technology. Additionally, the source reported that Apple has also improved its overall app security by enabling a data protection function automatically, preserving any information transferred across these third-party app providers.
Another new resource that speaks to the iPhones updated security is the single sign-on (SSO) capability that will allow end-users to set a password once across applications that contain sensitive information. This option is especially useful for businesses that hope to safeguard the data employees might be accessing through the cloud because it can prevent code sharing.
The first step is securing the phone itself
None of the above options are innately secure, however. According to Toms Guide, its essential that end-users with a mind for safety make optimal use of their iPhones built-in security feature - the passcode.The source reported that its one of the easiest ways to prevent accidentally or intentional breaches of data. Additionally, the upgrades to the iOS 7 platform have provided end-users with new options for creating and maintaining security. Traditionally, the lock screen was protected by a 4-digit passcode. Now, after Apples latest upgrade, it is possible to set alphanumeric protection, utilizing ten or more upper- and lower-case characters and numbers.
Toms Guide noted that the 4-digit PIN code has 10,000 combinations, which is difficult to hack but not impossible. With the newest option, it is much more challenging for individuals to break through this defense. In addition to this new safety measure, the iOS 7 upgrade enables users to program how often the device will ask for authentication. Rather than the traditional method, which asked for authentication every time the screen was opened, the iPhone can be set so that it will lock on a timed interval instead.
Does it really matter?
According to Security Watch, mobile devices have become a major part of the lives of users everywhere. The source referenced a study by Sprint that reported how frequently smartphones are accessed on a daily basis, and the one unifying factor is the risk associated with information exposure.Because of the ability to access the Internet on the go, data security has become a constant concern that responsible individuals are having to overcome. Additionally, without utilizing passcodes and other features meant to preserve the integrity of stored information, issues with privacy are growing.
In order to preserve what Security Watch calls "our most personal computers," its important that smartphones are protected with verification features that are built into their operating systems. Additionally, it is possible to reinforce these safety precautions with password management software, which can provide an extra layer of defense against unwanted access.
Available link for download
Thursday, February 23, 2017
Windows Defender vs Security Essentials vs Safety Scanner
Windows Defender vs Security Essentials vs Safety Scanner
Microsoft loves to confuse their users as most people have found out using Windows 8. Not only was Windows 8 confusing, but Microsoft keeps changing how the new operating system works with every update.
One of the most confusing aspects to Windows 7 and Windows 8 is the anti-virus solutions provided by Microsoft. Should you use Windows Defender or Microsoft Security Essentials? What?s the difference? Also what is Microsoft Safety Scanner and why is that different from the other tool anti-virus tools?
In this article, I?ll explain the differences between the different anti-virus tools in Windows 7 and Windows 8 and where you can use each tool.
Windows Defender vs Security Essentials
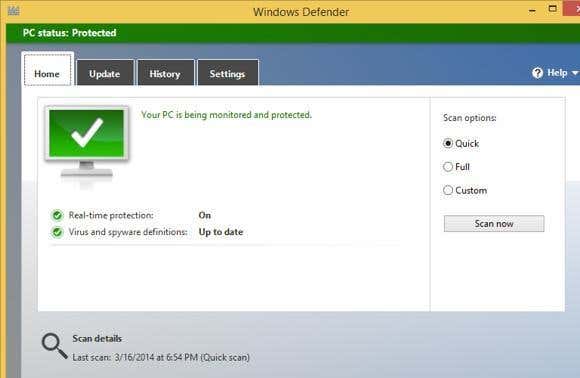
Windows Defender was originally known as Microsoft Anti Spyware and was eventually included with Windows Vista and Windows 7. You could also download Windows Defender for Windows XP and Windows Server 2003, though it seems that now you can?t anymore. You can still download Windows Defender Offline, which is different than Windows Defender and I?ll explain more below.
The main thing to note about Windows Defender is that it only protects against spyware in Windows 7 and below. That?s why you always needed another separate anti-virus program in Windows 7 and earlier. Microsoft Security Essentials could be downloaded to replace Windows Defender since it could catch spyware and scan for viruses. Once installed, it would disable Windows Defender altogether.
Windows Defender Offline is basically exactly what the name suggests: an offline version of Windows Defender that you download and run off a CD, DVD or USB drive. You can use Windows Defender Offline to scan for viruses before the operating system boots up, which can greatly help your chances of removing a very sneaky piece of malware or spyware. Again, it won?t catch viruses, just spyware.
In Windows 8, Windows Defender was upgraded to be able to do virus scans also. It pretty much is the same scanner as the one in Microsoft Security Essentials and that is the reason why Microsoft does not allow you to install Security Essentials on Windows 8. It also uses the same virus definitions and the user interface is pretty much exactly the same.
It might have made more sense to just keep the name Microsoft Security Essentials in Windows 8, but they decided to stay with the Windows Defender name, which causes some of the confusion.
So here?s the current state of Windows Defender:
- Comes built-in with Windows Vista and Windows 7 and only protects against spyware. Can be used with Microsoft Security Essentials.
- Comes built-in with Windows 8, but includes a virus scanner. Cannot be used with Microsoft Security Essentials.
- On Windows XP, you can use Microsoft Security Essentials as Window Defender is no longer available.
- Windows Defender Offline can be used on any version of Windows all the way up to Windows 8.1
Download Windows Defender Offline
Download Microsoft Security Essentials
Microsoft Safety Scanner
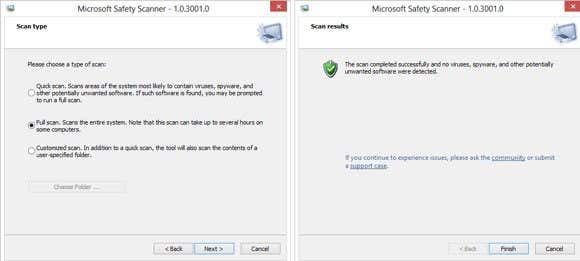
Microsoft Safety Scanner is another anti-virus tool from Microsoft that is similar to Windows Defender Offline in that it is a standalone virus and malware scanner. It?s basically an on-demand scanner that you can try to use as a last resort if the virus has disabled or interfering with your current antivirus program.
Unlike Windows Defender Offline, you still run Microsoft Safety Scanner inside of Windows rather than using boot media. You can simply download the EXE file which contains the latest signatures and run it. Since it?s an on-demand scanner, you should always re-download the program every time you want to use it otherwise you won?t be scanning with the latest virus signatures. The files are updated multiple times a day with the latest signatures.
Download Microsoft Safety Scanner
So hopefully that makes sense of some of the security tools provided by Microsoft. There are also other tools, but they are less common and we won?t mention them in this post. Windows Defender, Security Essentials and Safety Scanner are the main tools you can use for removing viruses and malware in Windows XP, Vista, 7 and 8. Enjoy!
Available link for download
Wednesday, January 25, 2017
USB Disk Security Latest and Full Version
USB Disk Security Latest and Full Version
Usb Disl Security Full Version
No need to activate just install and enjoy Full Version
Download Usb Disk Security Full Version

Available link for download
Monday, November 28, 2016
Tech privacy and security A debate we need to have Naked CIO
Tech privacy and security A debate we need to have Naked CIO
Its time to think hard about the attitudes of technology companies towards privacy and security.

Apple has announced it is fighting a court order in the US which would allow authorities to gain access to the contents of an iPhone as part of a terrorist investigation.
It amazes me that technology companies can put in place encryption that prevent these type of investigations ? yet under similar circumstances a warrant can allow authorities access to homes, cars and personal effects without condition or compromise.
But this incident is just one of many that involves tech companies and privacy.
And the flip side is that so many other tech companies cite the importance of privacy and security when it suits them but yet collect, aggregate, sell, decipher and use personal data to forward their own strategic and financial goals.
They track location, usage behavior, habits and desires in order to benefit advertisers and support their own business and application development. Their privacy policies even mitigate their liability from the collection and security of this data and in some cases limit their responsibility for securing customer information.
The fact is these tech companies survive and grow on disseminating personal information where is suits them, yet seem to want to be community activists when it doesnt.
They can achieve this through slick PR campaigns around encryption and fighting authorities on information disclosure ? to offset the multiple legal battles in European courts and beyond that deal with customer privacy.
Years ago at a symposium a question was posed when Google was in its formative stages. Do you fear Google? It was an interesting question with even more interesting answers. I stood up and said Yes, because the moment you dont fear them you could regret it. By fearing them you recognize their ability to be too big and too influential within the fabric of our lives.
Regardless of your geopolitical opinions these are fundamental question that needs to be asked. Are we now at the point where we have allowed these companies to own too much of our data without the recourse to reign them in?
As IT leaders within organizations that invariably collect information it is our duty to ask those questions of ourselves, too.
Information is valuable yet we need to be able to balance the need to understand our customers better with the basics of protecting their privacy.
At what point do we cross the line between collecting information to better inform decisions on business needs, and storing and analyzing data on individuals that compromises their understanding of what is appropriate?
The Naked CIO is an anonymous technology executive.
Available link for download
Thursday, November 24, 2016
Strengthen the weakest link in your IT Security System
Strengthen the weakest link in your IT Security System
|
Available link for download
Monday, October 31, 2016
Top 3 Selections for You When You Forgot Yahoo Password and Security Question
Top 3 Selections for You When You Forgot Yahoo Password and Security Question
As for Yahoo users, the Yahoo account means everything to you. With a Yahoo account, you can use all the Yahoo service such as Email, Messenger and Answers. In order to use the Yahoo account, you have to type correct Yahoo ID and password at the same time. If one of them is incorrect, you cant login the account successfully. However, sometimes we may have trouble remember them. Some users may forget Yahoo ID, while others may not able to remember the login password. What?s even worse, a part of them may even forget the security question. In this post, we will talk about it.

The Yahoo ID is actually the Yahoo email address, and the password is created and remembered by you, Yahoo will not keep your login password. That is to say, once you register a Yahoo account, you have to remember the Yahoo ID and login password correctly, otherwise, you are not able to continue login your Yahoo account. Well, you are not expected to see that situation occurs. Therefore, try your best to handle with this problem and take it seriously is your responsibility.
What to Do When You Forgot Yahoo Password and Security Question?
If you forgot Yahoo password and need to login the account urgently, what will you take action to do? Most of the persons have learned that they can make use of the security questions, but not everyone is so lucky to remember his or her security question and answers. Fortunately, there are still other options you can take advantage of.Selection 1: Reset Yahoo Password with Mobile Number
When you register Yahoo account, you have to type the mobile number and that is required to type in, you cant leave it blank. Otherwise, you will not sign up the Yahoo account now. Consequently, once you forgot Yahoo password and the security question, you can reset it soon.Step 1: Click the "I cant access my account" on the Yahoo login page from the computer and then it will jump into another page about your account problem.
Step 2: Select "I have a problem with my password" and then click the "Next" button. Then it will skip to another page and require you to type the mobile number.
Step 3: Type your mobile number and then click "Next" button, then Yahoo will send a verification code to your phone. Then you will see another page that allows you to type the code.
Step 4: Copy the code and paste it to the textbox, then you can reset your Yahoo password successfully.

Selection 2: Recover Yahoo Password with Optional Recovery Number
The Optional Recovery Number is appeared when you create the new Yahoo account. But it is different from the Mobile number because it is not the required field. Therefore, if you have filled in it and remember the recovery number, you might as well ask for help from it and try it right now. The steps are similar to selection 1, so good luck to you and hope you are able to recover your Yahoo password successfully.Selection 3: Crack Yahoo Password with Yahoo Password Recovery Tool
Another method to help you when you forgot Yahoo password and security question and answers is to make use of the third party Yahoo password recovery software to crack it. One of the best and frequently-used tools is SmartKey Password Recovery Bundle. It is a toolkit that included approximately 22 different password recovery tools. And you can try the Firefox Password Recovery or Internet Explorer Password Recovery to deal with your Yahoo password problem.How to Download This Smart Yahoo Password Key
Way 1: If you are interested in how to use this powerful password recovery toolkit that is made from SmartKey software, you can Google search and visit and download from its official website.Way 2: You can click the image as below and secure download and then install it from CNET download page as well:

How to Use This Professional Yahoo Password Recovery Software
You can know how to use it from its official guide page, or watch this video guide about how to use SmartKey password recovery bundle to recover Yahoo password when you forgot it:Available link for download
Tuesday, October 25, 2016
USB Disk Security Full Version Blogspot
USB Disk Security Full Version Blogspot
USB Disk Security Full Version Blogspot

For more information:
USB Disk Security is a program that protects against any malicious programs trying to attack via USB storage devices (USB drive, USB drive, memory card, USB, Flash drive, Flash drive, Flash memory, Flash cards, security cards Digital, the mobile storage device, the iPod, the music player). Compare USB Disk Security against other antivirus solutions, you will find the highlights of the program: USB Disk Security provides 100% protection against any threats via USB drive, while the product failing to ensure 90%. USB Disk Security is the best antivirus product to help protect offline computer without the need for signature updates, while other programs need to update the database regularly, and they identify can not effectively protect for offline computers.
Key benefits and features of USB Disk Security application:
- Blocking of threats from known and unknown multimedia content to be removed.
- The best solution to protect offline computer.
- Prevention blocking access of illegal users for the purpose of stealing data.
- Compatible with other security software.
- Compatible with all popular Windows platforms.
- the fastest security software and lightest.
- free updates.
- Blocking of threats from known and unknown multimedia content to be removed.
- The best solution to protect offline computer.
- Prevention blocking access of illegal users for the purpose of stealing data.
- Compatible with other security software.
- Compatible with all popular Windows platforms.
- the fastest security software and lightest.
- free updates.
The salient features of USB Disk Security products:
100% protection against poisoning programs via USB drive
USB Disk Security uses innovative technology to block threats known or unknown via USB drive. This feature applies to USB drives, flash drives, secure digital card, removable disk, pen drive format, can remove the drive, iPod ...
USB Disk Security uses innovative technology to block threats known or unknown via USB drive. This feature applies to USB drives, flash drives, secure digital card, removable disk, pen drive format, can remove the drive, iPod ...
The optimal solution to protect offline computer
Other antivirus software require updating virus database regularly, and they can not effectively protect offline computer that is not connected to the Internet. When new viruses, worms and other malicious attacks, the traditional symbol is not enough. Every minute wait a malicious virus update symbol will create a notification window to attack with clear consequences. USB Disk Security application uses interactive technology improvements, and close the window being attacked by the feedback based on signs and other reactions.
Other antivirus software require updating virus database regularly, and they can not effectively protect offline computer that is not connected to the Internet. When new viruses, worms and other malicious attacks, the traditional symbol is not enough. Every minute wait a malicious virus update symbol will create a notification window to attack with clear consequences. USB Disk Security application uses interactive technology improvements, and close the window being attacked by the feedback based on signs and other reactions.
Data protection
Provides high levels of protection against theft and unwanted loopholes losing confidential data. This feature can prevent individuals illegally copying your data to USB drives, and at the same time blocking of threats from USB drive.
Provides high levels of protection against theft and unwanted loopholes losing confidential data. This feature can prevent individuals illegally copying your data to USB drives, and at the same time blocking of threats from USB drive.
Software security fastest and lightest world
With USB Disk Security, users will be completely satisfied with the scanning speed and detection of threats. Compare with other antivirus software and youll discover that these applications have the smallest size on the market today.
With USB Disk Security, users will be completely satisfied with the scanning speed and detection of threats. Compare with other antivirus software and youll discover that these applications have the smallest size on the market today.
USB Disk Security is compatible with other security software as well as most of the popular Windows platform. It is not compatible with antivirus programs is an issue of concern, however, compatible USB Disk Security is a comprehensive security software with the other.
Compatible with other security software
Incompatibility between antivirus programs is an issue, however, USB Disk Security is fully compatible with other security software. Supports Windows 7, Vista, XP, 2008, 2003.
Incompatibility between antivirus programs is an issue, however, USB Disk Security is fully compatible with other security software. Supports Windows 7, Vista, XP, 2008, 2003.
Easy to use
USB Disk Security has been specifically designed to operate efficiently without depending on the actual level of computer users. Users just need to install and no configuration interested.
USB Disk Security has been specifically designed to operate efficiently without depending on the actual level of computer users. Users just need to install and no configuration interested.
Free updates
Other antivirus products required to pay annual fees for updates. However, the main factor of USB Disk Security is a matter of time. Users can get the update in the future program is completely free.
Other antivirus products required to pay annual fees for updates. However, the main factor of USB Disk Security is a matter of time. Users can get the update in the future program is completely free.
How to Crack
Name: AAWB
Serial: 17751
Serial: 17751
Name: abrade
Serial: abrade
Serial: abrade
Name: ABSITE
Serial: 17,908
-------------------------------------------- ---------------------
Serial: 17,908
-------------------------------------------- ---------------------
DOWNLOAD
http://feeds.feedburner.com/BeautifulWordsAndFun
Available link for download
Monday, October 10, 2016
Top 10 Tips for Online Shopping Security
Top 10 Tips for Online Shopping Security

Here we lay down few safety procedures which once you ensure will make your experience equivalent to one that you have while visiting your nearest mart for picking stuff up.
1) Your computing environment should be very secured
Almost a no-brainer yet half the online population neglects this as a safety step. When you make purchases online, everything is encrypted. So if your computer is not protected of malicious software, your financial information and passwords will be stolen (as a matter of fact everything stands the chance of being stolen that are saved in your computer). So it is the first thing to ensure that the firewall is on. Also adding to it, try avoid shopping online from cyber cafes or using a public network. Financial transactions are better done through trusted computers.2) Verify as to just how much you trust the store
There are correct ways of going about the shopping portal/ website you are trusting:- If you already know the outlet of the brand or store you are purchasing form, go-ahead and have trust. In case anything goes wrong during the financial transaction, you can always walk in to the relevant store and get the problem sorted.
- If you have friends or family buying from a particular store/ portal, there?s nothing to worry much in that case then.
- If you do not know the store at all, BEWARE! Keep your eyes open. Read customer reviews or best is, do the store?s background check by looking at sites dedicated to reviewing e-stores. You find your store there, go ahead and make your picks.
3) Avail discount
Why pay extra when there can be options o availing discounts. There are many sites like indianprice.com, etc. which provide massive discounts via coupon codes. They have lots of stores registered with them and if your chosen store is registered, there you go hitting the jackpot. Cross-check and who knows you might just be lucky!4) The too-good-to-be-true offers are not all that good always
You got no idea about the extent deceits can stretch. It?s not just on the online space but everywhere but when you are putting your money online, you can just be extra careful. It won?t hurt after all. Do not fall for the too-good-to-be-true offers. If they sound too unrealistic, there is no harm checking their reliability. They can be pretty unreal. Often purchasing from those sites can just be calling for bad luck. They can be low quality or stolen items or can also be cheap substitute of tall brands. The products might just never reach you or the portal merchant might just be playing all of it up for trading your bank details with someone else.5) Stay alert while buying a gift-card
It is always nice to make your dear ones happy with the fabulous gift cards which are available online these days. But always read the terms and conditions carefully when buying one. Also, ensure the store from where you are buying is legitimate.6) Do not trade too much of information
If the purchasing site is asking more information than you think is required, back off. It clearly is not reliable. The reliable sites would not go beyond asking name, contact details, email address, some method of payment, and at max your interest/ hobbies. But if you come across ones asking for driver?s license number, bank account information, social security information, etc. be cautious. It is a fraudulent one. There are hints that the merchant resell, rent or share your information. Alternatively, check the site?s privacy policy.7) Make a unique password if required
Often online purchasing stores ask you to create an account with them. You need not do it but just in case it seems important to you or easy, then carry on. But ensure you choose a very strong password for the account. Make it unique.8) Go a step high to ensure the security of the site
Hold on! Just before you enter any personal or credit card info onto a shopping site please do look at the URL. See if the web address on the page begins with "https:" and not "http." That little ?s? tells you the information is being encrypted to protect your information.9) Wiring money through Western Union or Money Gram is not suggestible
Reliable sites generally do not make it a mandate for you to pay through wires. It is always wise to pay via credit or debit card. Wiring is suggestible to people you know but not to random strangers. So do not take the risk unnecessarily.10) The grammar matters!
Might just sound very funny but do read the content that has gone on the website. If the content hosted by the portal/ the site is full of errors, typos, poor content, you can already sniff danger. They are not professional.All in all, novice shoppers who are going to just start buying online should better stick with well known brands and famous online shopping portals rather than breaking their head in the smaller, less known ones. Once you get a grip of the online shopping fundamentals, you can always start your journey towards becoming the pro online shopper. But till then, have patience.
Author Bio:
This is a guest article contributed by Ajeet Sharma who works for IndianCoupons.com - a coupon site helps user shopping online by providing discount coupons, promotional codes and deals for all major online shopping stores.Available link for download
Subscribe to:
Posts (Atom)


